Hardware attacks, a lingering threat for connected objects
Viruses, malware, spyware and other digital pathologies are not the only way computer systems’ vulnerabilities are exploited. Hardware attacks are not as well-known as these software attacks, but they are just as dangerous. They involve directly exploiting interaction with a system’s electronic components. These sneak attacks are particularly effective against connected objects. Jean-Max Dutertre’s team at Mines Saint-Étienne is committed to developing countermeasures as protection from these attacks.
[divider style=”normal” top=”20″ bottom=”20″]
This article is part of our series on Cybersecurity: new times, new challenges.
[divider style=”normal” top=”20″ bottom=”20″]
Enguerrand said: “Ok Google, turn on the light!” and there was light in the living room of his apartment. Voice commands are one of the sales advantages of Philips Hue connected light bulbs. They also offer the possibility of changing the room’s colors and scheduling lighting settings. Yet along with these benefits comes the setback of heightened vulnerability to cyber-attacks. In May 2017, a team of Israeli researchers presented various loopholes in these bulbs at a conference in San Jose, California. The researchers presented a typical case of an attack on connected objects used in everyday life. According to Jean-Max Dutertre, a researcher in the security of electronic systems at Mines Saint-Étienne, “this work clearly illustrates the Internet of Things’ vulnerabilities to hardware attacks.”
Cyber threats are often thought of as being limited to viruses and malware. Yet hardware attacks also pose a significant threat to the security of connected objects. “This type of attack, unlike software attacks, targets the hardware component of electronic systems, like the circuits,” the researcher explains. In the case of Philips Hue lamps, the scientists carried out an attack by observation when a bulb was being updated. When the lamp’s microcontroller receives the data packets, it must handle a heavy load. “The Israeli team observed the power this part consumes,” Jean-Max Dutertre explains. Yet this consumption is correlated with data processing. By analyzing the microcontroller’s power variations based on the data it receives, they were able to deduce the cryptographic key protecting the update. Once this was obtained, they used it to spread a modified version of the update to the other bulbs in the series by using the same key and successfully control them.
“In a non-protected electronic circuit, this type of attack works every time,” says the researcher from Mines Saint-Étienne, who is working to counter this type of attack. But hardware security is often forgotten. Either inadvertently or due to ignorance, many companies put all the emphasis on protecting software using cryptography. “The mathematical algorithms are secure in this respect,” Jean-Max Dutertre admits, “but once it has become possible to access the hardware, to observe how it reacts when the system processes information, this security is compromised, because the cryptographic keys can be deduced.”
And this involves many risks, even for seemingly insignificant connected objects. In sending a false update to the connected light bulb, the light bulb can then send back information to the attacker which includes the user’s personal information. Knowing when a light bulb is lit during the day reveals when a person is home, and consequently when they are absent. This information can then be used to plan a burglary. An attacker can also cause the manufacturer economic losses by making an entire series of connected bulbs unusable. Finally, it is also possible to make many light bulbs send requests to the manufacturer’s sites, thus saturating the servers, which can no longer respond to real requests—this is referred to as a denial of service attack. This causes economic problems for the company, but also negatively affects the real users, whose requests, sent by their light bulbs, cannot be processed. This therefore reduces the quality of service.
Fighting hardware attacks
What measures should then be taken to prevent these hardware attacks? At Mines Saint-Étienne, Jean-Max Dutertre and his team are first working to master the different types of attacks, developing an in-depth understanding in order to provide better protection. In addition to the attack by observation, which involves watching how the hardware reacts, there is also the attack by disturbance. In this second case, the attacker voluntarily disrupts the hardware while it is processing data. “A quick disturbance of the power supply of the integrated circuit or even the laser illumination of its silicon die will change a bit or byte of the data it computes,” the researcher explains. The hardware’s reaction when it processes the modified data can then be compared to its reaction when it processes unaltered data. This difference again makes it possible to determine the encryption keys and access the sent information.
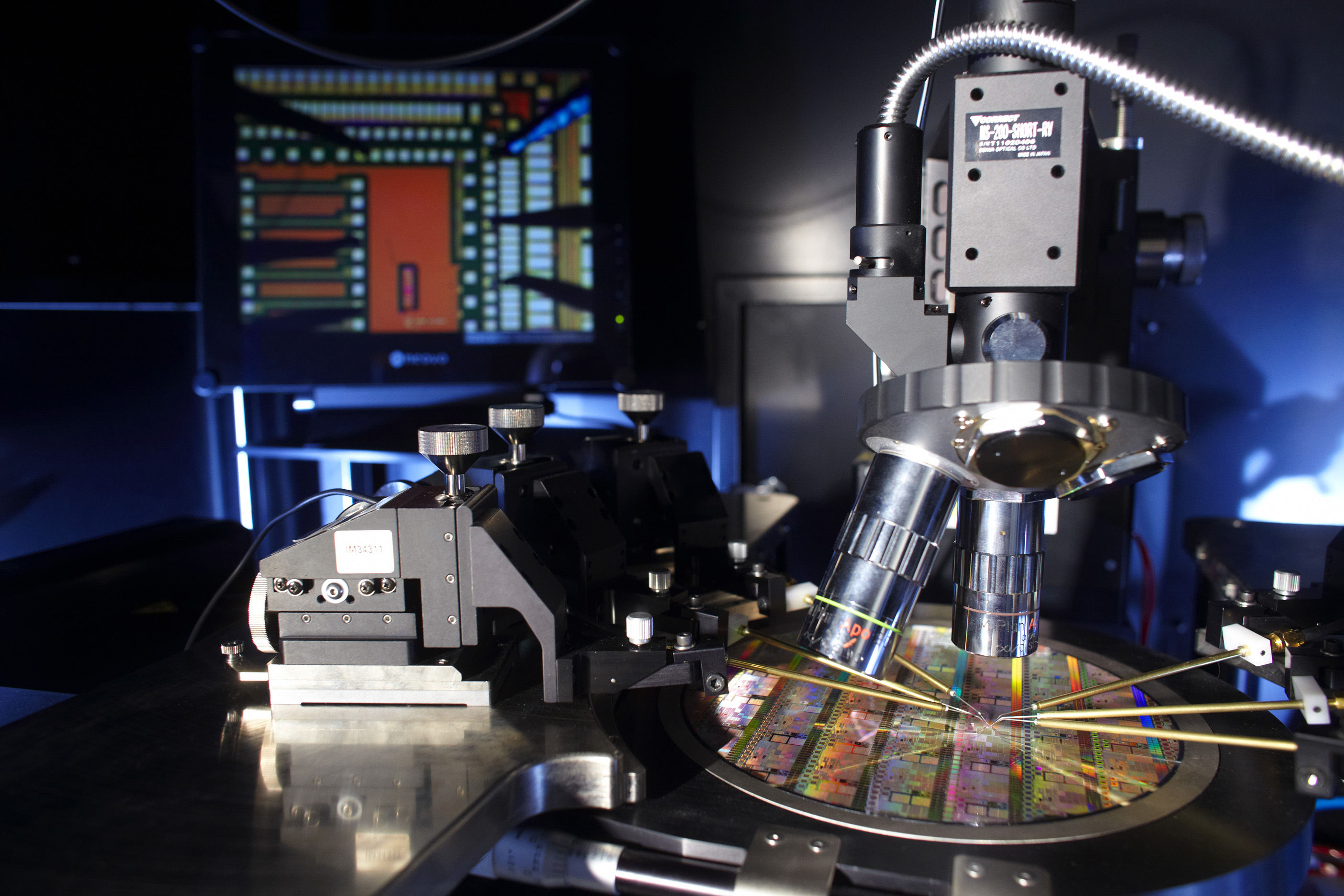
In the laboratories at Mines Saint-Étienne, the researchers use lasers to inject faults into the electronic systems. This provides them with a better understanding of their behavior in the event of a hardware attack by disturbance.
There are several countermeasures for these two kinds of attacks. The first and main category involves preventing the statistical processing of the device’s operating data which the attacker uses to deduce the key. “For example, we can desynchronize the calculations that a connected object will make when it receives data,” Jean-Max Dutertre explains. In short, this means running codes and calculation operations in a way that delays or staggers them. This makes it harder to understand which task is linked to a more significant activity performed by the connected object’s processors. Another possibility is hiding the data, performing calculations on hidden data and revealing them once the operation is completed. The attacker can therefore not obtain any information on the hidden data and cannot gain access to the real data. The second countermeasure category involves changing the hardware directly. “In this case, we directly modify the circuit of the connected object, by adding sensors for example,” explains Jean-Max Dutertre. “These sensors make it possible to identify disturbance attacks by detecting a laser signal or a change in the feed.”
Major component manufacturers and connected object manufacturers are increasingly beginning to consider these countermeasures. For example, the Mines Saint-Étienne team works in partnership with STMicroelectronics to improve the security of the circuits. However, smaller companies are not always informed about hardware faults and have even less knowledge of solutions. “Many startups do not know about these types of attacks,” the researcher observes. Yet they represent a large community among connected object manufacturers. In Europe, regulations on cybersecurity are in the process of changing. Since 9 May, all the Member States of the European Union must implement the directive on the security of networks and information systems. This provides in particular for the strengthening of national capacities in cybersecurity and better cooperation between the Member States. In this new context promoting technical advances, the way these hardware security threats are considered is likely to improve.
In the meantime, the researchers at Mines Saint-Étienne are continuing to develop new measures to fight against these attacks. “It is quite fun,” says Jean-Max Dutertre with a smile. “We set up methods of defense, and we test them by trying to get past them. When we succeed, we must find new means for protecting us from ourselves.” It’s a little like playing yourself in chess. Yet the researcher recognizes the importance of scientific collaboration in this task. “We need to remain humble: sometimes we think we have found a strong defense, and another team of researchers succeeds in getting round it.” This international teamwork makes it possible to remain on the cutting edge and address the vulnerabilities of even the most powerful technology.




Leave a Reply
Want to join the discussion?Feel free to contribute!